InfoSec Guide: Mitigating Email Threats
In spite of the surge in popularity of social media sites as well as instantaneous messaging, email is still an essential interaction device for company.…
View More InfoSec Guide: Mitigating Email ThreatsFive biggest security technology trends for 2020
For a long period of time business have actually been mainly worried about protecting themselves against exterior cyber risks such as viruses and cyberpunks. Yet…
View More Five biggest security technology trends for 2020Is Big Data Enough for Machine Learning in Cybersecurity?
Data is much more significant as well as prevalent now than it has actually ever been– as consumers, we’re currently at a 2.5-quintillion-bytes-of-data-per-day level. Risk…
View More Is Big Data Enough for Machine Learning in Cybersecurity?Infosec Guide: Defending Against Man-in-the-Middle Attacks
The network framework works as the major method through which customers within a company connect as well as share details. This makes it an especially…
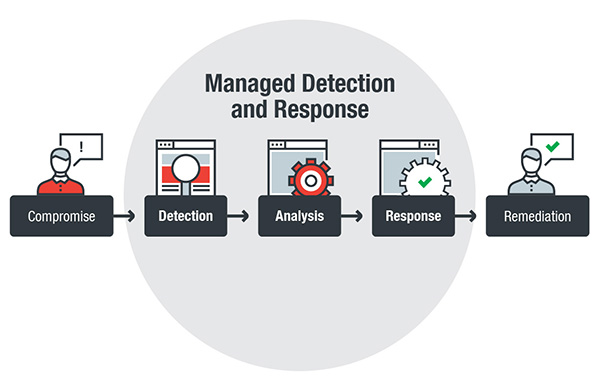
View More Infosec Guide: Defending Against Man-in-the-Middle AttacksBridging Cybersecurity Gaps with Managed Detection and Response
Handled detection and also reaction makes it possible for a positive technique to security with its ability to identify as well as totally assess risks…
View More Bridging Cybersecurity Gaps with Managed Detection and ResponseApache Struts Users Urged to Update Against Remote Code Execution and DoS Vulnerabilities
Customers of Apache Struts are encouraged to upgrade to the most recent version of Commons FileUpload library to avoid remote code implementation and denial-of-service (DoS)…
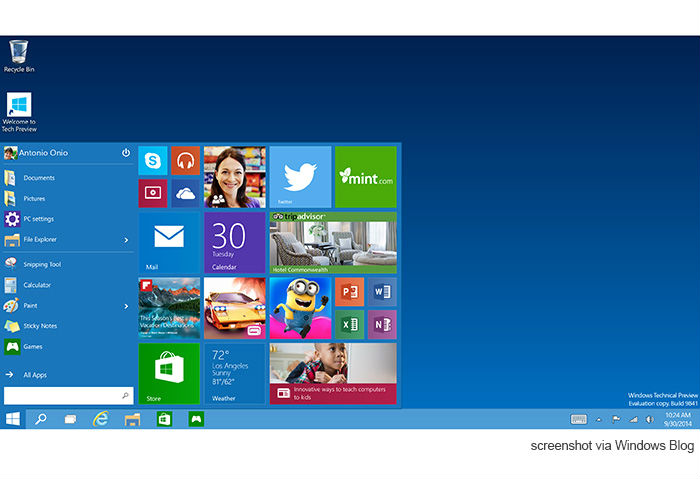
View More Apache Struts Users Urged to Update Against Remote Code Execution and DoS VulnerabilitiesHello, Windows 10: Security Features You Need to Know About
Microsoft’s much awaited Windows 10 is lastly below. After months of public beta testing, excited individuals can now update to what’s being regarded as Microsoft’s…
View More Hello, Windows 10: Security Features You Need to Know AboutNetwork Threats Examined: Clustering Malicious Network Flows with Machine Learning
When it comes to the risks they posture to enterprises, Network risks are industry-agnostic. Now that cybercriminals are progressively utilizing evasion techniques to bypass rule-based…
View More Network Threats Examined: Clustering Malicious Network Flows with Machine LearningSMiShing Attacks Leverage Punycode Technique
Protection scientists warn that homograph assaults– also called punycode method– are ending up being more commonly made use of for SMiShing to trick individuals, take…
View More SMiShing Attacks Leverage Punycode TechniqueMaking Computer Technology Available To The Masses
With the rapid expansion and improvement of information technology, and its impact on all aspects of life, the need to master computers is no longer…
View More Making Computer Technology Available To The Masses